5 Common Ways Malware Infects your Computer
When it comes to the many different dangers lurking in cyberspace, the threat of a nasty malware infection is always going to be one of the top threats you’ll face online.
We’re constantly seeing new strains and revisions of malware introduced into the wild, and threats like Cryptolocker and GameOver Zeus illustrate that malware authors are always looking for the latest, innovative ways to catch people out.
There are a number of ways your computer can become infected with malware. However, despite there being many thousands of different strains of malware lurking online, the fundamental methods in which they can infect a computer are thankfully much smaller.
Whilst the social engineering tricks used to ensnare a victim change on a daily basis, once you can spot the template or pattern of a particular malware scam, you will be much more successful when it comes to identifying and thus avoiding an infection.
So here we describe 5 methods used by scammers to infect a computer with malware.
Deceitful Website Downloads
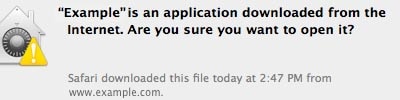
If you have contracted a malware infection from somewhere, the likelihood is high that you were tricked into downloading something from a website that was best left alone.
With the Internet being the most prevalent way malware scammers reach their victims, it is perhaps no surprise that websites with malicious payloads are the most common method used to lure a victim into downloading harmful files.
However your Internet browser and your computer software should prevent files from downloading to your computer automatically, without your consent (unless the criminals are using an exploit or vulnerability, see further down) so the website will use any of several methods to trick a user into downloading and running malicious files on their computer.
This really is an entire subject on its own merit, so we’ve got a separate blog post here detailing the different methods these criminals utilise to trick their victims into downloading harmful files to their computers.
But of course the best advice here is to avoid consenting to the download of files when visiting any website that you do not trust.
Malicious Email Attachments
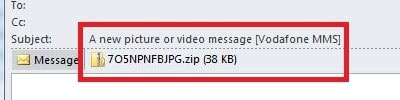
If a scammer can’t lure a victim into downloading malware from a website, they always have the option of sending malware straight to their email inbox as an email attachment.
Again your software, like your email client or web browser, will prevent these attachments from opening automatically when you open the email. You need to explicitly open the attachment and run it before your computer will become infected.
It is likely that the attachment will be in a ZIP compressed folder, hiding the true contents from security software that would block the attachment otherwise.
These scam will use various social engineering techniques to trick the recipient into opening the attachment. For example the email will claim the attachment is a courier deliver notice, or an invoice, or that is contains information relating to a fine or charge you’ve incurred. These are techniques aimed at luring the recipient into opening the attachment.
You can read a handful of email attachment tricks that are popular over Christmas in our blog post here.
Sponsored Content. Continued below...
Spammy Software, Apps and “add-ons”
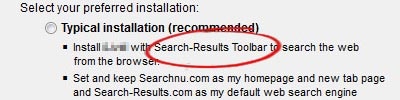
On the Internet there is no shortage of free programs, apps and other software that you can download. But free often comes at a cost, and in many cases this means downloading attached “sponsored programs” that are really nothing more than malware.
In more legitimized methods, the software you are attempting to install will give you the option to download additional software, or lure you into the “recommended install” that includes these additional programs. This is often in the form of adware or a browser redirect software that advertises third party software, some more reputable than others.
Less legitimate software will just go ahead and download third party software without your consent or knowledge.
Other software will simply perform additional, undesired commands, which is popular on the mobile app market.
And then there is malware which is referred to as Trojan horses, which is essentially malware disguised as legitimate software.
Naturally the advice here is to only install software from trusted sources, and research any software download prior to installation.
A Pre-existing infection
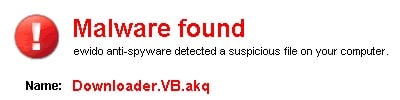
In cyberspace, malware often leads to more malware.
If you managed to get your computer infected with some type of malicious program, including via any of the aforementioned methods, this program can provide a “back door” to your computer than can lead to further – often more serious – malware infections.
This is popularly described by the term botnet, where scammers control a network of infected computers and can both control them remotely and install further malware on them. The notorious GameOver Zeus malware in 2013 was a key factor in the propagation of the even more notorious CryptoLocker ransomware that encrypted a user’s files and demanded a ransom to decrypt them.
The answer – run regular anti-virus scans with your security software to ensure your computer is clean and ensure your security software is up-to-date.
Exploits and Vulnerabilities
Software isn’t infallible to intrusions, and even if you’re doing everything you can to protect yourself, you can always be susceptible to an exploit, which is a vulnerability in a piece of software that could allow a criminal to compromise a victims computer without the usual pre-requisite for the victim to fall into a trap themselves.
Exploits are often referred to as “zero-day exploits” when the criminals discover – and exploit – them before the software developer discovered them and thus able to provide a fix.
Most software developers – including Microsoft, Adobe and Apple – provide regular updates to keep their software secure, so make sure you download them when they become available. There is little protection against zero day exploits, but downloading these updates in a timely manner will protect you from recently discovered (and subsequently fixed) vulnerabilities.
We’ve popped a version of this article on our YouTube channel which you can watch here!
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X