Facebook Phishing Scams
We discuss how Facebook phishing scams work, the methods in which they trick victims and how to avoid them.
Facebook phishing scams employ a variety of tricks to dupe victim’s into handing over their sensitive information (i.e. username and password). All phishing scams work by a scammer setting up a trap to make the victim unaware that they are about to pass their sensitive information straight to a scammer.
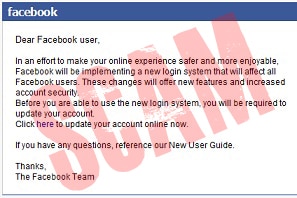
In nearly all cases, Facebook phishing scams work by sending a victim an email or message that links to a spoof website that attempts to trick a user into entering their Facebook username and password, which are then sent to a scammer. Take a look at the screenshot below.
If you thought it was the Facebook login page then you’re not alone. However the page does not belong to Facebook at all, but a scam website designed to trick users into thinking it is Facebook. The web address (we cut out the address in the photo above) actually reveals the page belongs to a foreign domain.
The number one, vital, imperative, golden rule, is that you ONLY, EVER enter your Facebook login details on Facebook.com. Sometimes scammers use tricks to try and make it appear like the site is hosted on Facebook – such as
1. login-information-facebook-com.ocsco.pw/facebook-login (editor note: fancy words do not distract that this domain is ocsco.pw, not Facebook)
2. facebook.ffaceboook.com (editor note: domains that look similar to Facebook are still not Facebook)
3. verify-your-facebook-login-details.tk (editor note: Facebook don’t create domains for every instruction they wish to give. Just because a domain includes the term facebook, doesn’t mean it belongs to Facebook)
Information entered into these sites are stolen by scammers, who then have access to your account and can do any number of nefarious acts using your account. Variants of these scams may not choose to duplicate the log-in screen, but instead will look like other official looking Facebook pages that may ask for other information as well.
Spotting a Facebook Phishing Scam
The easiest way to spot a phishing scam before it’s too late is – as we point out above – to take a look at the website address of a webpage before entering any personal details into it.
However there are other telltale signs that you can spot before you even get to the spoof website, such as how the scam reaches you in the first place. Facebook phishing scammers will use a wide variety of common tricks and ploys to try and fool a victim into clicking a link that leads to a spoof website. Next we outline a few.
Examples of Facebook Phishing scams
Phishing scammers are known to commonly use several types of templates to trick victims into handing over their personal information.
Someone Added a Photo. This phishing scam is sent via email and informs the victim that they have been tagged in a photo. The email provides a link to the email so the victim can see the photo. However the link goes to a spoof website designed to look like the Facebook website. The spoof site requests a user enter their username and password. This information is then stolen by a scammer. The social engineering aspect of this example is designed to trick victims who would naturally want to see what photos that they have been tagged in. After clicking the link in the email they are then forwarded to a spoof website that requests that they login. However this website steals the information that is entered into it.
Your Profile Has Been Updated. Emails sent to a victim that assert that the victims profile has been updated. In this example the email also claims that the victim has a “new message from Facebook Support”. The email appears to have been sent from Facebook Support. The social engineering aspect of this example is that the user will want to see what the message from Facebook Support says, so they will click on the link, which leads to a spoof website that requests the user login. The websites then sends the username and password to the scammer.
Account Disabled for Abuse/Violations. This example involves a Facebook Chat message sent from an already compromised account (that has had the name changed to Facebook Security or similar) to another Facebook account and asserts that the user has had their account disabled for abuse or a violation. The message contains a link to a spoof website that requests that a Facebook user enters their personal information (including username and password) in order to reactivate their account. The social engineering trick in this example clearly being that a victim will want to reactivate their account for fear of losing it so will comply with the message and unwittingly enter all of their sensitive information into the spoof website where it will then get sent to the scammer.
Updated login/security features. This example is sent to a victim through email and will claim that the victim’s Facebook account has been updated and the victim will need to visit Facebook through the link to update their account. Again this email will link to a spoof website that requests a user enter all of their Facebook details (including password and username) which is then duly stolen. Again this example relies on a similar social engineering trick as the last example as the Facebook user will comply with the message for fear of not being able to use their Facebook account.
Fake friend Requests. This example is again sent via email and asserts that there is activity you missed on Facebook. The email implores users to click the link to see what activity it was that they missed. In the case of this email the messages assert that the victim has 2 friend requests. The social engineering aspect is designed to make the victim curious as to who has sent them the requests and will thus click the link in the email and will be asked to login to a spoof website, where the victims username and password will then be stolen.
Facebook Messages. This example, again sent via email, asserts that the user has unread Facebook emails, messages or notifications, depending on the specific example. Of course the social engineering aspect here is aimed to make the victim curious as to what those messages or notifications are, and thus the victim will feel compelled to click the link to find out. Once again they will be directed to a spoof website that requests the user logs in to their Facebook account, and once again it steals all information that is entered into it.
In all of the above examples the victim is directed to a spoof website that steals all of the information that is entered into it. This is only a small section of phishing scams used against Facebook users. There are plenty more phishing scams and templates used on the Internet every day.
Avoid Facebook Phishing Scams
To avoid these scams users are advised to be wary of any communication such as emails or chat messages they receive from Facebook and by extremely cautious if such communication contains link to another website.
Always check the URL address of websites before entering your Facebook password to make sure it begins with www.facebook.com. Facebook will only ask you to enter your password on the facebook.com domain so if you are on another site then you are certainly looking at some kind of phishing scam. The same applies to any other sensitive information you enter into websites.
And remember having good, reliable security software can block phishing websites and help keep you safe. For our recommendations, click here.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X