5 ways you can get a malware infection – and how to prevent them
The consequences of a malware infection can be potentially devastating, with more advanced types and strains being released into the wild every day.
Malware types such as ransomware can be particularly devastating should they infect your device, since this can lead to the loss of all your personal files, including photos and music.
Cyber-crooks are always looking for new tricks and techniques to get nasty malware on to your computer. And while the specifics of their tricks and techniques are always changing, they can still be broadly categorised.
We list the different ways you can wind up with a malware infection and – more importantly – how to prevent it from happening.
Tricked into downloading it from a website
Perhaps the most common way of infecting a computer with malware is by getting the user to download and install it from a website themselves. After all, that saves the crook from having to get past a user’s security software.
Now, a crook can’t usually automatically download and open something to a user’s computer because their Internet browser won’t allow it, and of course a user isn’t going to knowingly download malware. So a crook has to trick the user into thinking a download is safe, when it isn’t.
For example, this can be achieved by –
Fake antivirus/scareware. When browsing a website, a pop-up window will appear warning the visitor they have been infected by a virus and they need to download software to remove it. The warning is fake and is simply trying to trick the visitor into believing they’re downloading antivirus when what they are really downloading is malware.
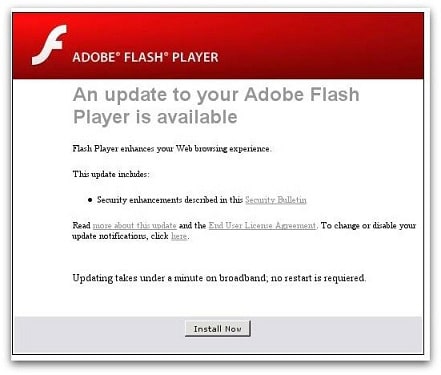
Fake flash/video plugins. Sites will use this social engineering trick to try and lure a victim into downloading malware under the belief it is a Flash update or an update for a video player.
Links on social media. Such links may promise the victim something, but will lead to external websites that are interested only in installing malware on a computer.
To prevent this from happening…
NEVER download anything when visiting a site you don’t trust, even if it looks legitimate. That is the golden rule. Just because a pop-up looks safe, if it’s asking you to download or open something, assume that everything is dangerous. In these cases, we flip the popular adage on its head – now it’s guilty until proven innocent. Updates from programs like Flash can be obtained from their official website.
Sponsored Content. Continued below...
Email attachments
Another popular way of infecting devices with malware is through the use of dangerous email attachments. Crooks will use a variety of social engineering tricks (many we outline here) to lure an email recipient into opening an email attachment and subsequently infecting their computer.
Ransomware is popularly distributed this way. The email attachment can take on a number of guises, including JS (Javascript) files, VB (Visual basic scripts) BAT files or even malicious Microsoft Office documents that will either download dangerous macro files or execute what is called a DDE attack.
![]()
Watch out for suspicious attachments.
To prevent this from happening…
The simple rule is this; only open email attachments when both of the conditions below are met –
1. You know the sender
2. You were explicitly expecting them to send over a file attachment.
Unless both of those conditions are met, you should assume an email attachment is dangerous. If you know the sender but were not expecting them to send over a file attachment, contact them in person or over the phone to verify the attachment.
Zero-day exploits or “drive by” downloads
The software we use every day is never perfect, and can contain vulnerabilities that can be exploited by cyber-crooks. If the criminals discover those vulnerabilities before the good guys, then that is what we call a zero-day exploit.
Such zero-day exploits can vary in how dangerous they are, but a worst-case scenario could mean that merely using software that has been exploited could be enough to get infected with malware. If your Internet browser has been exploited, this can also lead to “drive by” downloads, which means merely visiting a webpage is enough to result in a malware infection, with no download permission box needed.
To prevent this from happening…
There is little you can do to avoid a zero-day exploit, since this means the crooks are exploiting a vulnerability yet unknown to you or the developer of the software you’re using. This is why it is so important to have reliable, up-to-date antivirus on your computer as another level of defence against online nasties.
Also, once a developer discovers a vulnerability, they should soon patch it up with a security update. So to minimize your chances of being caught out by software vulnerabilities, always ensure all the software you use is up-to-date.
Sponsored Content. Continued below...
Bundled software
This refers to legitimate programs that have an installation process that will ask (or maybe not ask) you to install other software alongside them.
This method is common with a type of malware called a PUP, or Potentially Unwanted Program. This often means those pointless toolbars or an alternative search engine. However it can also mean other more serious types of malware.
To prevent this from happening…
Only install software from sources that you trust. This is because even if the software you’re installing it legitimate, if it’s from an untrusted source, they could have bundled it with unwanted software, even malware. Also, pay close attention when installing software to check if it wants you to install any other “sponsored” programs that you may not want.
Pre-existing infection
It is worth noting that many malware infections are the result of existing malware infections. If you have been infected with malware already, this can act as a “back door” that allows crooks control of an infected device, giving them the power to install more malware onto a computer.
Some types of malware infections are designed to be completely invisible, as the crook doesn’t want the owner on an infected device know they’ve got malware. This is popular with “botnets”, which refer to a network of infected computers all controlled by a master computer, operated by a criminal, to achieve an end goal.
To prevent this from happening…
Regular full virus scans with your security software should make sure you don’t have any existing malware infections.
These represent the most common ways malware can infect a computer. There are, however, other methods. For example using torrent software to download files, tech support scams, or using infected removable storage devices which was a popular method of distributing malware before the days of the Internet.
The most important aspect to avoiding malware infections is by educating yourself. Once you know how malware infects a computer, you already know how to avoid it. Don’t be a stranger to cybersecurity.
Also worth checking out… for our recommended security software, click here.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X