There are many different ways you can end up with malware on your computer, but following the below 5 simple steps can help protect you against the most common methods that crooks use to infect devices.
It won’t come as much of a surprise that most malware comes directly from the Internet. Usually this means it is downloaded when you’re surfing websites via your Internet browser. A common misconception is that this usually happens automatically, without you realising. In fact the opposite is true. In most cases, the user agrees to download the malware. Of course they are most likely unaware it’s malware they are downloading. With the exception of serious security vulnerabilities, crooks can’t automatically download and execute files via your web browser onto a computer. The user needs to give their permission.
Crooks use a variety of tricks to lure victims into agreeing to download files. This includes fake “virus detected” pop-ups, (see image below) pop-ups asking you to update your video player to watch a video, downloads claiming to offer features or cheats for video games, dangerous torrent files and fake software updates. It can also include mobile apps from unknown sources outside of the Google Play and Apple stores.
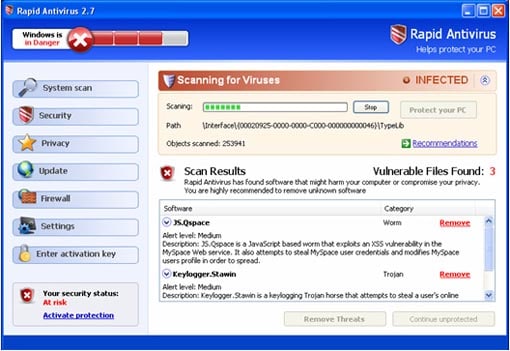
Pop-ups will try and lure you into installing malware.
The request to download appears legitimate so the victim downloads the file, opens it, and gets infected with malware.
To avoid this, if you get an unexpected request to download something, don’t do it. Investigate first. How did the request appear? Was it a pop-up when visiting a website? Do I trust this website that is asking me to download a file? Do I know this file or this website is legitimate? If you’re not sure, seek help from someone more knowledgeable before agreeing to download anything.
Sponsored Content. Continued below...
Despite this being the far simplest method and the easiest to warn against, malicious email attachments remain one of the most prolific methods of infecting devices. And that’s because crooks can craft very convincing social engineering tricks to lure email recipients into opening email attachments they shouldn’t be opening, just like the email below.

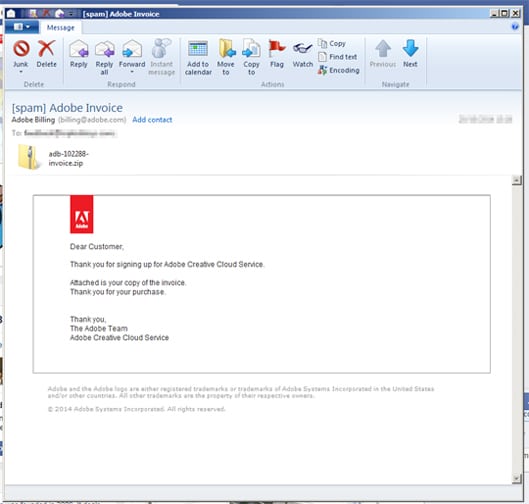
Emails may claim to have an invoice for you to trick you into opening malicious files.
This can include targeted emails, specially crafted to make them appear to look like something a specific recipient might expect to see in their inbox.
Be wary of all emails that contain attachments and ask you to open then. Even if that email appears to have come from a friend. Verify with the sender if the email is legitimate, and only open attachments that you were specifically expecting to be sent as a particular time.
Windows XP was great. One of Microsoft’s best operating systems. But it hasn’t been supported for years. This means when serious security vulnerabilities are discovered (and they often are) Microsoft won’t fix them.
It’s the same for all unsupported software. Vulnerabilities are particularly dangerous, because if crooks are exploiting them, a person can still get infected even if they are following good security habits. Vulnerabilities in software offer the crooks a way in – one that doesn’t rely on a victim doing something they shouldn’t be doing, which is how most other malware attacks work.
If software is no longer supported, you shouldn’t be use it. This is especially true of old operating systems (like XP) and Internet browsers.
Sponsored Content. Continued below...
If the software you use it still supported but you don’t install the updates, then you’re at the same risk as if you were using unsupported software. Updates often contain security fixes for known vulnerabilities, so make sure you install updates when they become available.
Most software will default to automatic updates, including your Internet browser and operating system. It is recommended to keep that option enabled and to restart your computer once prompted (for Windows updates.)
There are lots of great antivirus software solutions out there, both free and premium. While Windows computers do come with antivirus software preinstalled, it’s always best to add to that security. Antivirus software can help protect you against security vulnerabilities and can help you if you do fall for a scam, but they shouldn’t be solely relied upon – you still need to follow good security habits! Our recommendations for good security software is here. And lastly, backup your data! Data loss as a result from ransomware is at an all time high, both for businesses and personal users. Our recommended backup solutions are here.
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X