7 of the most notorious computer viruses of all time
Code Red
Named after Mountain Dew Code Red because that was what the security researchers that stumbled upon this computer worm were drinking at the time, this virus harks back to 2001 and affected devices running the Microsoft IIS (Internet Information Services) software.
Code Red wasn’t particularly disruptive, and it targeted a well-known type of vulnerability called a “buffer overflow”. What made this malware so iconic however is that is changed what it did based upon the date. Between the 1st and 20th of the month is would spread from device to device automatically using known flaws in the Microsoft IIS software. After the 20th it would then turn all devices it infected into a giant “botnet” (see more on botnets here) to initiate a DDoS attack (more on DDoS here) on the White House website.
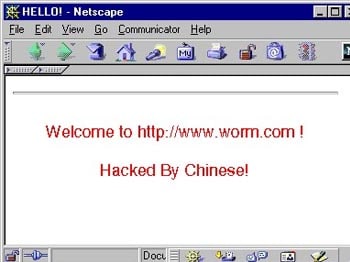
Infected machines would often display a message reading “welcome to Worm.com. Hacked by Chinese“.
MyDoom
Released in 2004, MyDoom is often attributed with the dubious honor of the most destructive malware in computing history due to the damages involved in recovery that were estimated to be in excess of $38 billion (yes, with a ‘B’!) It’s almost one of the fastest ever computer worms where at its peak around 25% of all emails being sent globally carried with them the MyDoom malware. The malware even took down Google for a day, preventing users from performing web searches.
The malware primarily used a ‘failed delivery email notification’ social engineering trick to lure recipients into opening a malicious email attachment.
The malware, upon infection, would install a backdoor on a device, affording the malware control of an infected device. Infected devices were harnessed into a botnet to attack targets with DDoS attacks, namely the SCO Group. The worm contained the text “Andy; I’m just doing my job, nothing personal. Sorry.”
So prolific was the malware that emails today are still bouncing around carrying the MyDoom malware, though thankfully much less than in 2004. The author is unknown.
Sponsored Content. Continued below...
Stuxnet
Released in 2010, the Stuxnet malware was reportedly created by American intelligence services and Israeli intelligence services and originally designed to target facilities in Iran suspected of supporting Iran’s nuclear ambitions. The malware was specifically tailored to exploit vulnerabilities in software used at industrial and energy sites. It was reported to have caused significant damage within Iran.
It has since mutated and subsequently deployed to attack other types of industrial facilities.
Morris Worm
The Morris Worm is accredited with being one of the earliest examples of malware and the very first malware attack that received any type of mainstream media attention. It was created by Robert Tappan Morris, a student as the Massachusetts Instritute of Technology and let loose back in 1988.
It wasn’t designed to be destructive; instead the mere 99 lines of code was dedicated to spreading the worm between device and device, which it did with little trouble given that the industry of cybersecurity didn’t really exist – at least not in the same way it does today.
However the worm did prove to be trouble because of one flaw in the design. It would infect devices that had already been infected, meaning it reverberated around the Internet (which by then contained only around 60,000 devices) multiple times, clogging global connection speeds until large parts of the Internet grinded to a halt. It is estimated the worm infected around 10% of cyberspace.
Morris himself always maintained his worm was a computer experiment gone wrong.
What other viruses or other malware attacks do you think belong on this list?
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
