Will Zuckerberg remove Hillary Clinton from Facebook for 50k likes? It’s a hoax.
A post on social networking site Facebook is spreading virally that claims to show a screenshot…

A post on social networking site Facebook is spreading virally that claims to show a screenshot…

In terms of computer security, we often here the term “vulnerability”, such as “the attacker exploited…

A video is going viral across the Internet that claims to provide a “secret hack” that…

We all have those signs or signals that tell us that a certain part of the…

Internet company Yahoo have confirmed reports that a staggering half a billion (!) user accounts have…

Like-farming describes the various methods spammers, even criminals, use to attract followers to their Facebook pages,…
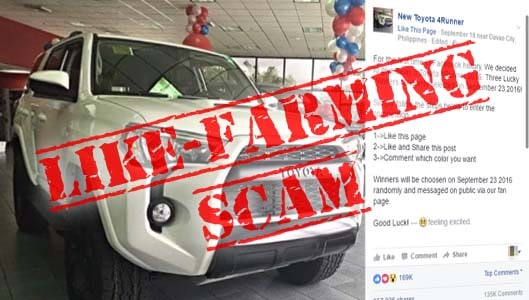
Despite what a Facebook post may claim, you’re not going to win a free Toyota 4Runner…

Email users should be aware of a popular scam campaign luring victims into opening up dangerous…

Anyone who has been in a large social media group chat will know how annoying they…

Posts imploring you to help locate missing children by sharing photos of them are a common…