Could this finally be the end of Office macro-distributed malware?
In welcome news, Microsoft has announced that it will take crucial steps from April this year to help curb one of the most prolific ways that crooks spread computer malware across the Internet; through Microsoft Office documents laced with macro malware.
But first things first. Let’s briefly recap Microsoft Office macros and what they have to do with malware.
What are Office macros?
Microsoft Office users have the ability to create little files of programming code called macros, and embed them in the Office documents they create (e.g. Word, Excel, PowerPoint). Why? Because macros allow users of a particular document to perform certain automated tasks that the program (again, Word, Excel, PowerPoint) couldn’t do otherwise.
Macros are essentially small files that can expand what an Office program can do with a document. They’re generally considered an “advanced user” feature, given that you need to know how to code a macro (and indeed have a complex enough reason to need one in the first place.)
Microsoft Office macros can be programmed by anyone with the relevant know-how, and embedded into any Office document of their choosing. And therein lies the problem. Macros were soon being exploited by developers of malware.
Sponsored Content. Continued below...
A brief history of macro malware
When macros were first used to distribute malware, back in 1995, it was a well-known “fact” that you could only infect your machines with malware by opening a .exe file or .bat file. However macro laced malware destroyed that myth. With macros, not only could malware infect your computer by opening an Excel or Word document, but crooks found it much easier to persuade victims to do just that because, after all, what harm could opening an Office document really do?
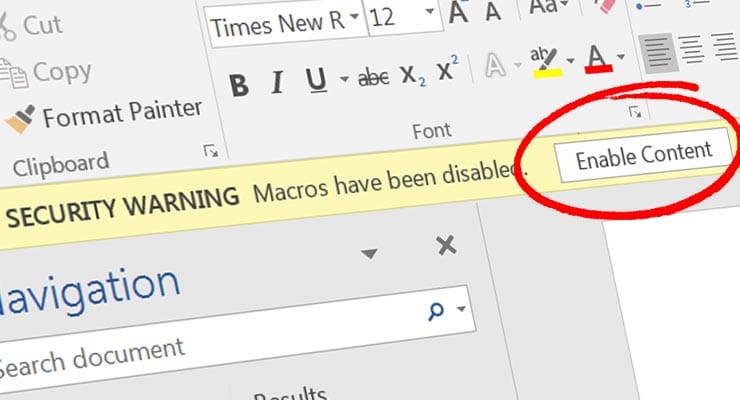
Well, if that Office document was laced with poisonous macros, then it can do much harm indeed. It wasn’t long before Microsoft stopped macros from running inside an Office document by default, instead asking a user if they wanted to enable Macros once they opened the document (below).
This was good because it stopped dangerous macros from running as soon as the Office document was opened. However, crooks later pioneered a number of convincing social engineering tricks to convince victims not only to open an Office document, but also to enable macros as well.
Sponsored Content. Continued below...
Which brings us to this news.
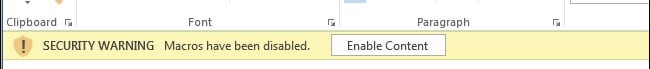
From April 2022, Microsoft has announced that Office documents received from the Internet will now replace the yellow “do you want to enable Macros” dialog bar (like the one above) with a more urgent red dialog bar informing the user that Macro’s have been disabled (e.g. the one below.)
![]()
There will be no one-click resolution here. Instead, users will need to click the Learn More button taking them to a page on the Microsoft website explaining the dangers of macro malware. If users still want to enable macros, they’ll be given instructions on how to do it that involves saving the document to their local hard drive and going into its properties.
These hoops a user needs to jump through are intended to make it significantly harder for crooks to create social engineering tricks to lure a victim into enabling macros. The more steps a user needs to take, the higher the chances they’ll not bother or determine that this is nothing more than a scam.
The ultimate hope here is that with these extra steps, the success rate of macro-distributed malware will become so low that the crooks will abandon this method altogether and finally we’ll see some sort of end to this attack method that has been so prolific for over 25 years.
Of course we’ll have to wait and see if this proves true.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X