Emails lure recipients into downloading malicious Excel files
A series of email scams are attempting to lure recipients into infecting their devices with malware downloaded from the Internet in the form of malicious Excel documents.
The malicious email campaign, that also targeted several of our mailboxes, used a variety of common yet often effective social engineering tricks to trick recipients into infecting their devices. We take a look at one example of this scam from start to finish.
Step 1: The bait (the email)
The initial scam email landed in our inbox and claimed that we had a parcel waiting to collect with USPS, and for more information about that parcel, including to arrange a time to collect it, we needed to visit a webpage.
A screenshot of the offending email is below.
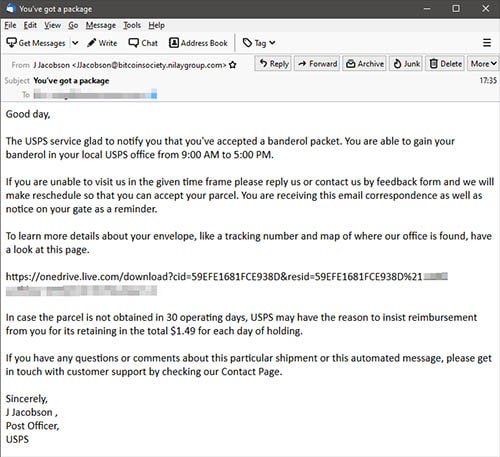
“Failed delivery” emails are a popular social engineering trick. They’re most frequently used by phishing scammers to lure victims to spoof websites that harvest sensitive user data. However in some cases, such as the example above, they can be used for malware attacks.
The URL in the email – partly blurred by us – leads to a Excel file hosted on OneDrive, which is Microsoft’s cloud storage platform. Note that the URL is not clickable. This may be intentional by the crooks to help their email bypass junk or spam filters.
Of course the URL can still be copied and pasted into a browser, and doing so will automatically download the Excel file to the device.
Sponsored Content. Continued below...
Step 2: The Infected Excel file
The Excel file will download to the user’s device automatically, but it won’t open, so currently there is no malware infection. But if the recipient – believing the social engineering story presented in the email in the first step – opens the Excel file, then they’re only one final step away from infecting their device with malware.
The last step is Macros. These are small files that Office applications like Excel can use to perform certain functions that they normally couldn’t. But these are security nightmares. Macro’s are downloaded from the Internet by the Excel file, and they can be coded by anyone, including cybercrooks. To put it frankly, if an Excel file uses Macros, the Excel file is potentially capable of downloading malware onto your computer.
That’s why Macros will be disabled by default. If a person opens an Excel file that needs to use Macros, the user has to manually agree to enable them.
Of course, that is exactly what the scam Excel file is going to ask you to do, as per a screenshot of it below.

The instructions on this particular Excel file advise the email recipient to enable editing and to enable content. This allows the Excel to download Macros.
And that is enough to infect a device with malware.
Sponsored Content. Continued below...
So the steps in this scam are –
1. The initial email luring a visitor into visiting a webpage.
2. The Excel file downloads and the victim opens it.
3. The Excel file tricks the victim enables content, thus downloading Macros and infecting their device with malware.
Don’t fall for these scams. Watch out for unexpected emails with stories like “failed delivery” tales, and never click links or copy & paste web addresses in emails, and finally, never enable Macros in Office documents that come from the Internet from untrusted sources.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
