How did hackers steal hundreds of celebrity photos?
A few years ago, hundreds of images – many sensitive – were stolen from various celebrities and uploaded online for the whole world to see, in an incident dubbed Celebgate.
Over the last few weeks, more photos were leaked online in what some are calling Celebgate 2.0.
But how are the cyber-crooks getting their hands on all these photos?
A number of theories circulated since the original Celebgate in 2014. And while many different scams all probably make an appearance in some of cases, it now seems that a good portion of these scams involved a simple social engineering phishing scam.
A simple phishing scam
One of the hackers involved in the Celebgate hacking scandal – Ryan Collins – admitted in 2016 that his method of obtaining the celebrity photos was using a simple phishing scam. This is a scam that requires a comparatively low level of technical knowledge and involves the victim actually falling for the scam for it to work.
This is how it worked –
Collins would send various celebrities an email that was designed to appear like it had been sent from Apple. The email would implore the recipient to click a link in the email and login to their iCloud account. It would trick recipients to do this using a social engineering trick, for example purporting that there was a security issue with the recipients iCloud account and the recipient needed to confirm their identity.
Sponsored Content. Continued below...
However the links didn’t lead to the iCloud login page. They would lead to a webpage owned by Collins that looked like the iCloud login page. The scam requires the victim to not know the difference, and enter their login details regardless. Those details are then sent straight to the criminal, in this case Collins.
Providing no extra security was enabled on the account – such as two-step authentication, Collins would have access to that account, where he was free to copy and download any photos stored on the account.
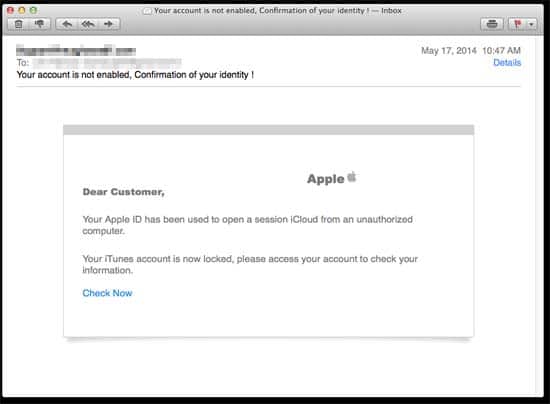
An example of an iCloud phishing email, similar to what Collins could have used to ensnare victims.
Phishing scams are immensely popular, and are not just used against celebrities. They can target just about anyone online, and be used to phish Facebook, PayPal, banking and eBay credentials, to name a few.
It is entirely possible that many of the celebrities were simply unaware that the photos taken on their iPhones were actually being synced automatically to their iCloud storage. This storage may still keep photos that have been deleted from the phone.
Other possibilities…
Before Collins’ admission, theories were spreading that suggested Apple’s iCloud service – which stores photos taken from an iPhone automatically – may have been compromised itself, possibly using a “brute force” attack which would allow a computer program to guess a password millions of times until it got the right one. A security glitch in the Apple “Find my phone” app would have allowed such an attack to take place.
However Apple denied this was the case and Collins’ confession shows that – in his case at least – it wasn’t a software hack of the Apple iCloud, rather a simple phishing scam that was to blame.
This isn’t the only way crooks could get their hands on stolen photos. The possibility that Apple’s iCloud was compromised in some way remains a possibility, though Apple deny it. Additionally, criminals could use credentials from previous data leaks that were re-used for an iCloud account. Basically, people using the same email and username for multiple accounts.
To protect your iCloud account –
Don’t use the same password as for other accounts.
Use a strong password.
Enable two-step authentication.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
