Cloning scams – otherwise known as impersonation scams – began their life on Facebook. But they’ve now moved to other social platforms – most notably the more open and potentially fertile lands of Instagram. Here’s how Instagram cloning or impersonation scams work on Instagram and how to avoid them.
They say impersonation is the sincerest form of flattery. But that definitely doesn’t mean you want crooks impersonating you or your friends on Instagram in this type of scam that’s still growing in popularity.
1. Create a duplicate Instagram account
Many users have their Instagram accounts set to public, especially when compared to Facebook. This means these accounts are easier to clone. Cloning an account really just means creating a brand new account and making it look like an existing account. It works when a crook essentially duplicates a legitimate Instagram account by copying their name, profile picture, mini-bio and some of the content they posted and plugging all that information into a brand new Instagram account in order to pretend to be a person they’re not. The scammer is trying to effectively take on the identity of the holder of the account they cloned.
The only thing a crook can’t duplicate exactly is the username, since usernames have to be unique. But crooks can most likely create a close copy, for example adding an underscore. Below shows the results after Jake Moore from We Live Security cloned his own Instagram account (the cloned account on the right.)
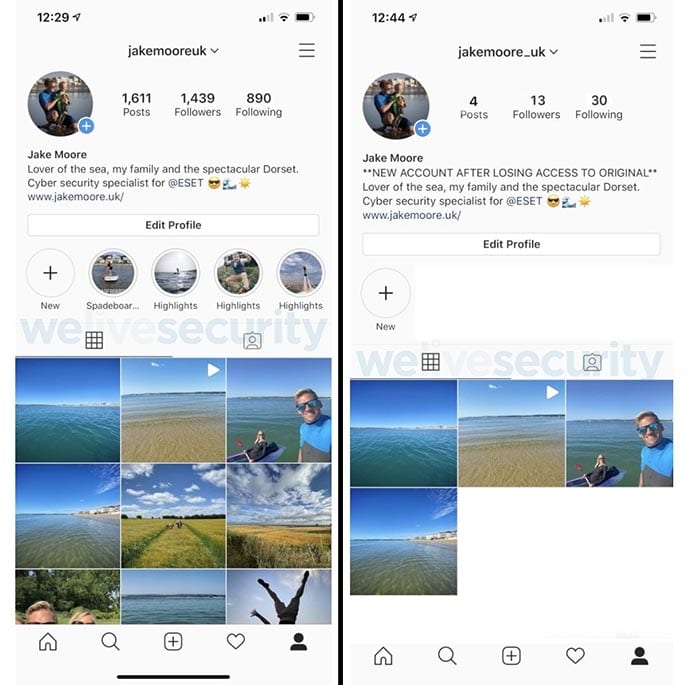
As you can see, the accounts look very similar, and most users won’t be able to spot any differences, especially upon a cursory glance.
Sponsored Content. Continued below...
2. Follow the original account’s followers
Armed with the duplicate Instagram account, the crooks then reach out to the followers of the original account by following them or sending follow requests. The crook – posing as the Instagram account holder they cloned – may claim they lost access to their original account and created a new one. Or they may say nothing and just hopes the accounts they follow just don’t realise or question anything about the new follow (or follow request.) The crook will also hope these accounts will now follow their cloned account.
3. The end game; the SCAM (usually asking for money.)
At this stage, the crook has created a near identical (clone) account of someone, and they’re now presumably following some of their friends too, and many of their friends may be following the cloned account in return.
The final step is the scam itself, which is initiated by sending messages while assuming the identity of the person whose account the crook cloned. The scam itself can vary, but more often than not it is a variation of the “friend in crisis” scam whereby the crooks create some emergency scenario and urge the people they message to send money – all the while taking on the identity of the person whose account they cloned.
Sponsored Content. Continued below...
The best way to deter crooks from cloning your account to target your followers is to make your account private. This prevents crooks from creating a convincing duplicate account, and also hides your followers list, so crooks would find it more difficult to know who to target if they did duplicate an account.
Of course many users don’t want to do that, so to make sure you don’t fall for a cloning scam watch out for duplicate accounts following you, or requests to follow you (if your account is private.) If you do see duplicate accounts following you, look at the usernames to spot the fake account.
If you’re not sure which account is a duplicate of the other, contact the person using another form of communication outside of Instagram.
And never send money after an Instagram chat with a friend or family member until you’ve independently verified it is indeed them. Again, this means contacting them outside of Instagram, preferably face to face or talking with them over the telephone.
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X