How crooks trick you into opening dangerous email attachments
Emails that contain malicious attachments are one of the most popular ways of spreading malware, including the particularly nasty ransomware.
Of course, for this type of attack to work, the crook has to use their email to persuade the recipient into opening the dangerous attachment, and they can’t just ask you to open the attachment and infect your computer with whatever malware is lurking inside the attachment.
So the email itself is the crux of the scam. It’s what we call the “social engineering” aspect of a scam. The scam’s ability to persuade a victim into doing something the crook wants.
We learn best by seeing real life examples of how crooks do this, so we present some of the most common social engineering methods crooks use.
You’ve been billed!
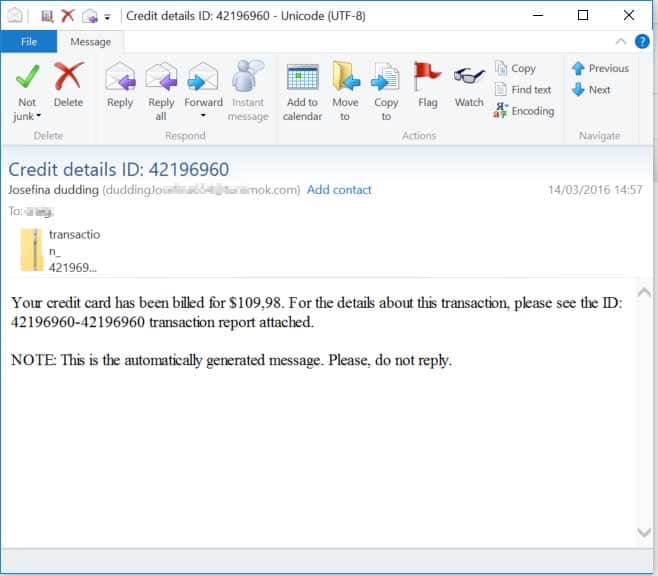
Nothing is likely to panic a recipient more than an email telling them that they’ve been billed for something they don’t recognise. Examples of emails using this tactic may look like an invoice with instructions on opening an attachment for more information, or an email simply claiming your credit card has been billed and to look at the attachment for more transaction details, as per below.
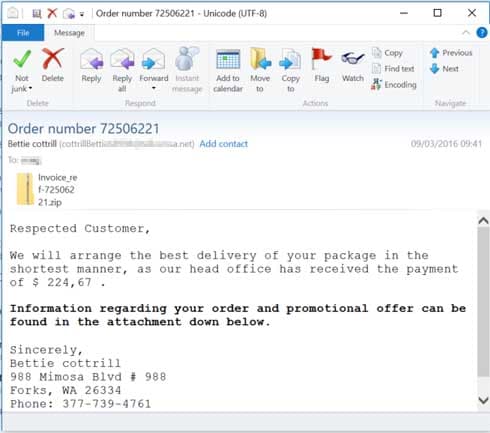
Or the email may claim to pertain to a recent order you’ve made, as per the example below.
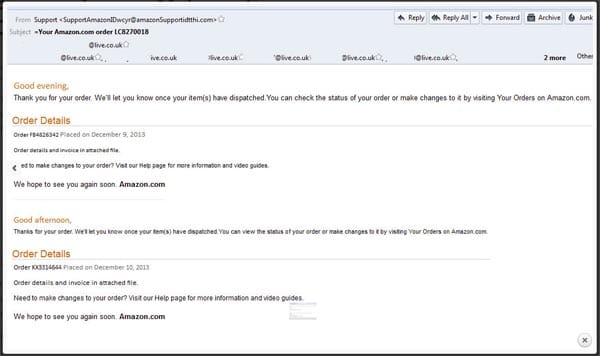
Alternatively the crooks could be particularly savvy and design their email to look like the invoice of a popular online retail company, like Amazon – again with details to open an attachment for more details on the alleged transaction, as per the example below.
You’ve received an important document
Crooks need to pique the curiosity of the recipient to increase their chances of getting them to open an attachment. An effective way of doing that is to claim the recipient has received an important document but provide no details as to what it pertains to. For example an email may claim you’ve received a fax document via email…

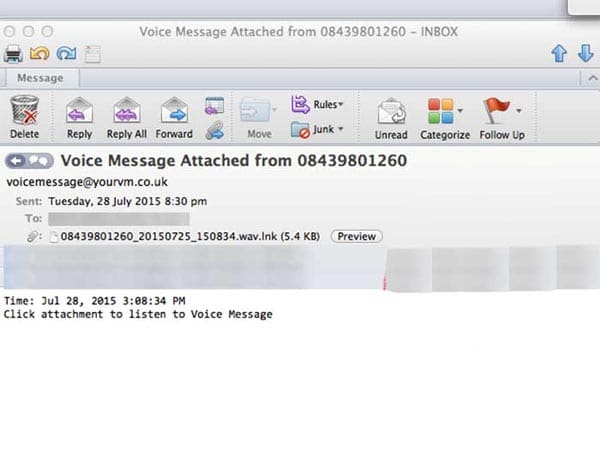
Alternatively the email may claim you’ve received a “voice message” or something similar, again providing no details to the specific nature of the attachment, so again piquing the curiosity of the recipient.
You’ve received this specifically alarming document
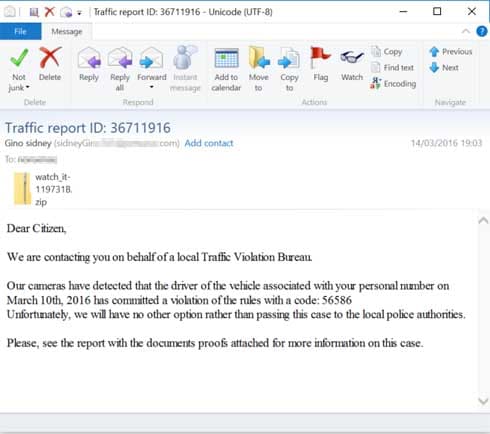
Being vague about an attachment may have its advantages, but another approach is to be more specific yet alarming. For example this savvy example that claims the recipient has violated a traffic law, the details of which are attached…
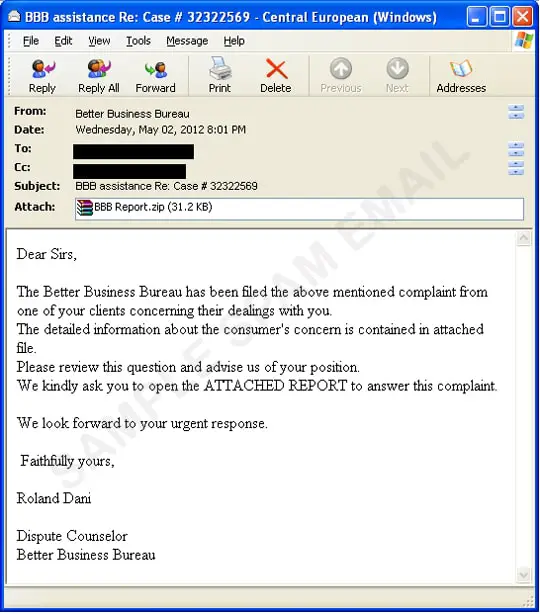
Or this example which claims a complaint has been made against the recipient to the Better Business Bureau, the details of which are attached.
You’ve received that document you could very well be expecting
Businesses are at a distinct disadvantage in the respect that crooks will know that businesses will typically be expecting certain emails to land in their inboxes, or at the very least a particular email wouldn’t look out of place.
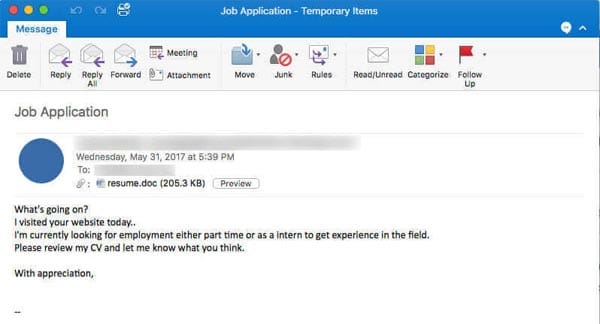
For example, an HR department could be expecting prospective employees to send their CVs, as per the example below…
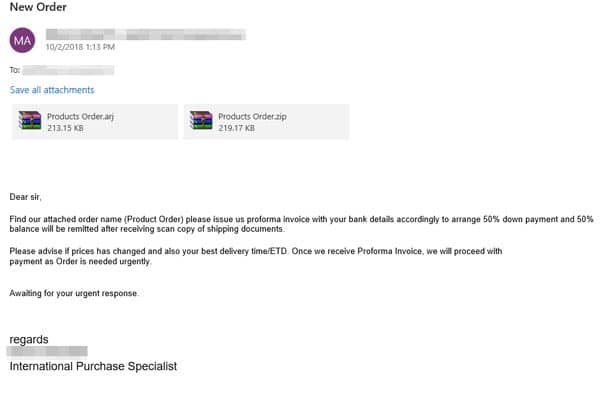
Or a finance department could be expecting emails concerning invoicing or problems with payments…
Emails tailored to businesses or specific departments in a businesses are half way to becoming a targeting phishing scam, often referred to as spear-phishing. This means a phishing scam has been tailored specifically to the recipient. The crook could add a business name or the name of an employee within the business to add even more legitimacy to their targeted scam.
Sponsored Content. Continued below...
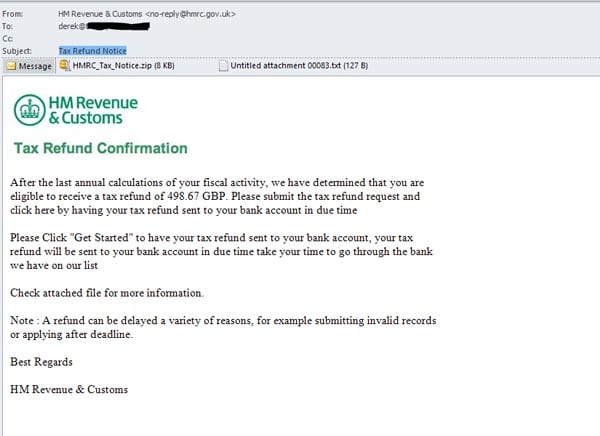
You’ve got a benefit
No one wants to pass up a freebie, like a rebate or reward. Crooks can also play on that by luring in potential victims by promising them money, like this tax rebate scam email which appears to be from the HMRC (UK tax authority.)
Super targeting spear-phishing
The hardest for a crook to set up, but by far the most difficult to spot form the recipients point of view, is spear-phishing.
Spear-phishing means the email has been tailored to fit the recipient specifically, and they can vary greatly, so providing examples would be pointless. What we can do is provide examples as to how a spear-phishing email could use tailored information to trick a recipient.
This can include –
– using the recipient’s name, address, date of birth or other personal information in the email
– spoofing the senders name or email to make it appear like a person known to the recipient, such as a friend or work colleague
– creating an email that the recipient would genuinely be expecting, such as forwarding a resume, or a report
The examples of emails above are only a tiny selection of the potential scams out there, broadly categorised. Of course, new email scams hit the cyber streets every single day, though most of them are variants or permutations of many of the examples above.
However once you learn how to spot them, and you’re familiar with the various examples of scam emails like the ones we’ve detailed above, avoiding the latest email scams can be made much easier.
The best way of protecting yourself from email malware attacks is to simply never open an email attachment until you have confirmed with the sender that the email is legitimate.
As a secondary defense, backing up your data and having reliable security software installed on all your devices is still very important.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
