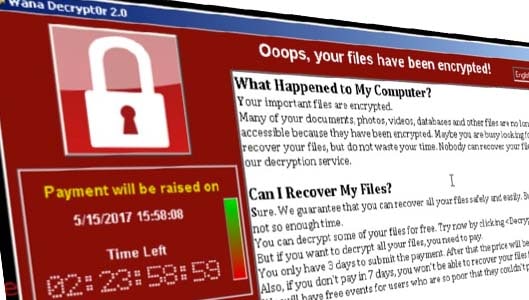
Lessons learned from the WannaCry ransomware attacks
As cyber communities everywhere begin to recover from last weekend’s widespread ransomware attacks, we take a look at why these attacks were so successful and what security lessons need to be learned.
On May 12th, the attacks began. By the time they began to subside, over 200,000 computers across 150 countries had been infected, including important parts of the UK’s National Health Service.
Dubbed WannaCry, this malicious strain of ransomware had encrypted countless files and had made the criminals over $70,000 worth of Bitcoins.
But why was this ransomware campaign so successful, and as such, what lessons do we all need to learn?
WannaCry used exploits, not social engineering
Perhaps the most important aspect of WannaCry’s success is the way it infected computers. While most ransomware attacks rely on a victim infecting their own computer – for example by being tricked into opening a dangerous email attachment – WannaCry was able to use exploits in the Microsoft operating system that allowed it to travel between computers without the unwitting help from the victim.
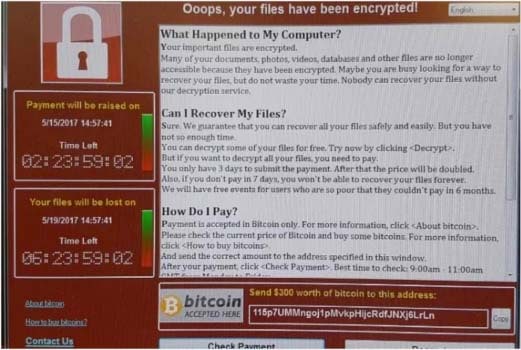
The ransom note displayed by computers infected with WannaCry
Those exploits were actually discovered by the NSA, who in turn wrote tools designed to capitalise on them. Those tools in turn were leaked on the Internet and used by criminals in the ransomware attack.
Microsoft had actually released a security update to fix the exploit over a month before the ransomware attacks. However any Windows computers that were set to apply updates manually but hadn’t, or any computers running Windows operating systems that are no longer supported (like XP) – were still susceptible to the exploit.
And it was these computers that found themselves infected with ransomware.
Sponsored Content. Continued below...
Out-dated or unsupported software is itself a vulnerability
As such, by far the most important lesson in all of this is the risk of using out-dated or unsupported software.
Computers running Windows that haven’t had the latest updates applied are out-dated. Computers running older operating systems like Windows XP and many versions of Vista are unsupported. Both are vulnerable to attacks that use software exploits.
In either case, the victim doesn’t necessarily have to be tricked into infecting their own computer with malware. The worst case scenario is that their computer can be infected with absolutely no help or intervention whatsoever.
The big lesson. Apply security updates promptly, and upgrade from unsupported operating systems. The same lessons apply to all software, such as your Internet browser, security software and mobile apps.
Backing up isn’t a buzz phrase. It’s something you actually need to do
Whether you’re a home user or a business, backing up is imperative. Not only because of ransomware attacks like this that renders files useless, but because there are a number of different ways that we can lose our files and need to recover them from a backup.
Given that we now know that the criminals made at least $70,000 worth of Bitcoins in this recent attack, it is clear that a number of people and organisations needed to hand over significant money to try and get their files decrypted, meaning they didn’t have a workable backup of those files.
If you have all your files backed up, a ransomware infection isn’t disastrous, just an annoyance.
Train yourself, train your employees (if you have any)
While these latest ransomware attacks spread primarily through exploits in Windows, most ransomware attacks still rely on the victims themselves clicking on dangerous links and attachments. Education is vital to stopping most ransomware attacks in their tracks.
It is important that you educate yourself and your employees about detecting and avoiding ransomware scams, including how to spot emails that are likely to contain dangerous email attachments.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X