Man tricks tech support scammer into infecting own computer
If you ever want to hear a tale of an Internet scammer getting their very much deserved comeuppance, then you may want to read this tale from French computer programmer Ivan Kwiatkowski.
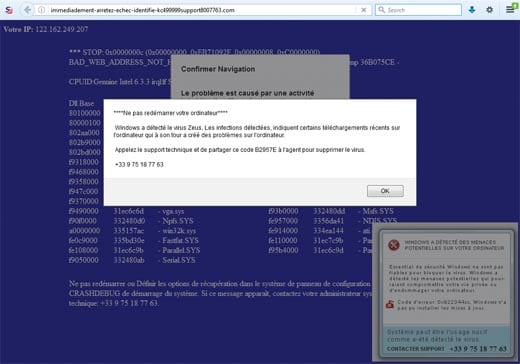
This story starts when Kwiatkowski’s parents managed to land on a suspicious website that told them that their computer had been infected with malware. This is the start of a pretty typical technical support scam, whereas the visitor is told to contact a “technical support” number for assistance on how to remove the threats from their computer.
But there are no threats. The website is simply lying to the victim to scare them, and the technical support number doesn’t go to any technical support department anywhere, rather it contacts the criminals.
Kwiatkowski’s parents contact him instead, and having a technical background, Kwiatkowski quickly determines the website is nothing but a scam, that – should you find yourself presented with a similar website (image below) – should be simply ignored.
However Kwiatkowski decided to investigate the scam further, in an attempt to see how it worked, so he contacted the support number given by the website.
After initially getting through to a pre-recorded message, Kwiatkowski managed to get through to a human, Patricia. As is standard with these sorts of technical support scams, Patricia guided Kwiatkowski into installing a remote-assistance program that gives her control to Kwiatkowski’s computer (Kwiatkowski was using an old Windows XP virtual machine for this “investigation”.)
Patricia proceeded to open CMD.exe, which opens up a DOS console window that are still present on Windows computers where you can type in DOS commands (see for yourself by clicking Start and running CMD.exe.) After entered various alarming commands like “ip hacked” and “1452 virus” (these are not valid DOS commands but Patricia is assuming the panicked victim isn’t going to know or notice) Patricia then tells Kwiatkowski that his computer has been hacked and needs to be cleaned.
Sponsored Content. Continued below...
This is the part of the scam where the scammer now tells the victim they need to pay for their antivirus program. This scam is a doubled edged sword, because not only does the scammer get the victim to give them money, but they also will then proceed to give the victim some (almost certainly) dodgy software that is probably some variant of malware in itself. Basically, the victim is paying to infect their own computer with malware.
Kwiatkowski quickly reaches for some dummy debit card numbers, but bizarrely when Kwiatkowski asks if he needs to buy the software from Microsoft, Patricia agrees, and the call ends. Kwiatkowski concludes that Patricia must be a “scammer trainee”. Kwiatkowski calls again, and this time gets through to Dileep who goes through the same procedures as Patricia did, but Kwiatkowski notes that Dileep sounds more experienced.
Dileep also claims that Kwiatkowski’s computer needs to be cleaned, and Kwiatkowski proceeds to give Dileep the dummy credit card details, which – of course – fail to process. Eventually Kwiatkowski persuades Dileep to receive a photo of Kwiatkowski’s credit card to obtain the numbers because “that may work”. However there was no photo. Kwiatkowski had just sent Dileep (via the remote-assistance program that allows the pair to exchange files) a sample of the popular Locky ransomware, zipped up but given the appearance of a jpg photo.
From Kwiatkowski’s blog of the incident –
I open my “junk” e-mail folder where I find many samples of the latest Locky campaign – those .zip files containing a JS script which downloads ransomware. I grab one at random, drag it into the VM. The remote-assistance client I installed has a feature allowing me to send files to the operator. I upload him the archive and say:
— I took a photo of my credit card, why don’t you input the numbers yourself? Maybe that’ll work.
At first, Dileep ignores me. He makes me type in my information a few more times (he’s persistent, I’ll give him that), until I put my foot down:
— Look, Dileep, I’m old and my sight is not so good. It’s starting to hurt, having to squint to read those tiny numbers. Also, we’ve established I’m no good with computers, how about you give me a hand here?
He says nothing for a short while, and then:
— I tried opening your photo, nothing happens.
I do my best not to burst out laughing.
— Are you sure? Sometimes my pictures have a problem opening on MacOS, are you on Windows?
— Yes, he replies. Your pictures are corrupted because your computer is infected. This is why we need to take care of this.And while a background process quietly encrypts his files, we try paying a couple more times with those random CC numbers and he finally gives up, suggesting that I contact my bank and promising to call me back next Monday.
Kwiatkowski obviously had some fun with this scammer, but assuming you don’t have a handy sample of the Locky ransomware available at a moment’s notice, what should you do if you come across such a scam?
The best advice is just to ignore those websites that tell you that your computer is infected and don’t click on any content within the website, and certainly don’t contact the number on the site. It’s just bait to lure you into calling a fake tech support number. As long as you didn’t agree to anything to install on your computer, the chances are that it isn’t infected with anything at all.
Make sure you have antivirus installed at all times and only trust notifications from that antivirus software when it comes to any sort of security notifications.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X