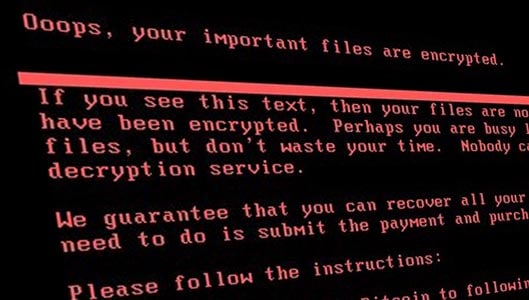
“Petya” ransomware goes viral. Here is what you need to know
As many in the cyber security industry correctly predicted, another global ransomware attack is going viral, infecting thousands of computers across the globe. Here is what you need to know.
What is ransomware?
Ransomware is a type of malware that encrypts the files on your computer so they cannot be opened. The encryption is so strong that in many cases you cannot regain access without a decryption key. The crooks behind the ransomware claim they will sell you the decryption key in return for BitCoins (a virtual currency you need to pay for.) For our full article on ransomware, click here.
What version of ransomware is it?
The version of ransomware is a permutation of earlier versions of ransomware spotted in 2016 called Peyta, which we discussed in a previous article here. However it is significantly different and the similarities may only be superficial, meaning many security experts are dubbing this recent strain of ransomware as “NotPetya”. Just like Petya, the ransomware encrypts both the files on a hard disk as well as the MFT table which tells your computer where everything is stored on the hard drive.
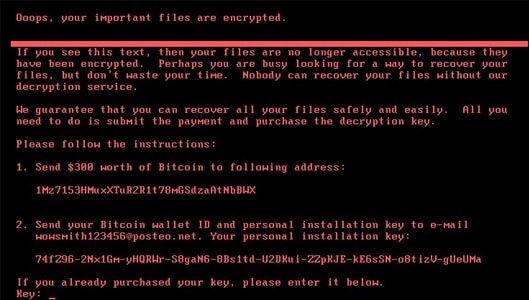
This is the screen on infected computers.
Just like the last global attack in May 2017 dubbed WannaCry, this “NotPetya” ransomware has been bundled with an exploit leaked from the NSA called “EternalBlue” to help it spread between computers that haven’t installed the latest Windows updates.
However, unlike WannaCry, this strain of ransomware also uses other techniques to spread between computers belonging to the same network. These techniques target the various Network Administrator tools available to network admins, and make this strain of malware more sophisticated in how it spreads when compared to the WannaCry attacks. First the ransomware attempts the EternalBlue exploit and failing that tries to spread itself using Network Admin tools.
Where did it come from
The people behind the ransomware are unknown, but it first surfaced in the Ukraine, where it was designed to initially spread through a software update from a popular accounting program used by the Ukranian government. Most of the reported infections are currently in the Ukraine and Russia but are spreading outside of those countries.
Who has been hit?
Lots of countries and businesses have been hit, including the Chernobyl radiation monitoring system, legal firm DLA Piper, food giant Mondelez, AP Moller-Maersk, WPP and Saint-Gobain. Luckily the UK’s NHS doesn’t appear to have been significantly affected as they were with the earlier WannaCry attacks. While lots of businesses have been infected, personal users are also at risk since the malware can infect any computer running a Windows operating system.
Sponsored Content. Continued below...
If I’ve installed the latest Windows updates, am I safe?
Back in March 2017 Windows actually patched up the exploit EternalBlue which is what both WannaCry and NotPetya both use to spread, and ensuring these updates are installed will greatly decrease your chance of getting infected.
But it doesn’t make you completely immune. This ransomware can spread through other avenues, such as through infected Office documents attached to emails, so having up-to-date antivirus software and knowing how to avoid malware is still essential.
Don’t pay up, you won’t get the decryption key
Paying up is controversial and no way a guarantee of getting your files back at the best of times. But in this case, there is literally no chance, since the email the crooks were using to communicate with victims no longer exists after the email provider pulled the plug on it. So don’t pay up, since there is no way the crooks can get you the decrypt key even if they were planning to in the first place.
Protect yourself
Normal rules apply here and you’ve probably heard it all before.
– Install the latest Windows and browser updates.
– Have reliable antivirus installed at all times who can protect you from the very latest threats (check out our recommended product here..)
– Never open email attachments unless you were specifically expecting one from a specific user
– Keep a current backup of all your important files
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X