Police Department pay cryptolocker criminals ransom
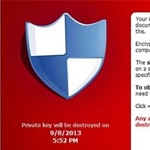
Last week we warned of a real threat facing Internet users, about a type of malware dubbed Cryptolocker that had the capability of encrypting files and forcing victim to fork over cash in order to obtain the decryption key.
This type of rogue malware, unlike its predecessors, is capable of shutting users out of their files, permanently, with the only solution to pay criminals a ransom to get their information back. That, or simply delete and lose their information. This makes this latest malware infection one of the more aggressive to date, with irreparable consequences.
And law enforcement has generally issued the advice that paying the criminals is not the recommended course of action.
But in an incident reminiscent of a Hollywood movie, it is law enforcement that have had their hands forced into paying up, handing over cash to the criminals in order to regain access to encrypted documents.
According to the Herald News, the Swansea Police Department in Massachusetts had their computer systems infected with the aggressive malware on November 6th, and have paid $750 via BitCoin to recover the lost documents. That is to say, the police have paid the criminals.
So of course the moral of this tale is that if a police department managed to get itself infected with this type of malware, then most users are vulnerable as well.
So heed the advice we issued last week – we generally don’t recommend paying the ransom, but if any file is worth paying for, then it should be securely backed up in case of an incident like this.
Also be cautious and aware of suspicious activity when on the Internet. Cryptolocker, despite being abnormally aggressive, will still infect computers through well-worn methods, such as malicious email attachments, malicious Internet downloads or through a backdoor provided by pre-existing malware.
Additionally make sure you are running up-to-date antivirus software – all the leading antivirus companies have issued updates ensuring their users are protected from this threat, including our recommended security software.
And the answer to many questions regarding removable storage – yes, it is possible for malware to infect external drives or USB drives if they are attached to the computer at the time of infection.
You can read our post on everything you need to know about the Cryptolocker malware here.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X