Ransomware explained. What it is and how to remove it.
Ransomware is one of the most prolific types of malware threats facing both businesses and individuals, in part due to its success in making the cyber criminals who develop it substantial amounts of money.
Ransomware differs from many other types of malware in that simply removing it from your device is only half the solution. Even after removal, victims of ransomware are likely to be left with the difficult predicament of how to recover their files, since ransomware’s objective is to make those files unreadable until the victim pays a ransom to recover them, hence the name ransomware.
Ransomware has been around for decades, though only became a prolific threat around 2012, at the same time as the rise of crypto-currencies such as Bitcoin. That is likely because such crypto-currencies provided an effective way for crooks to receive ransom payments from victims without leaving a money trail leading back to them.
How does ransomware work?
Ransomware is a type of computer malware that, upon infecting a device, will search for and encrypt certain types of files, making them unreadable to both the user of a device and the device itself. The files that get encrypted during a ransomware infection depend on the ransomware itself, but is typically personal files like text documents, images, music, spreadsheets, project files and videos. However ransomware can also encrypt file types specific to a particular business, or system files needed to make software on a device work correctly.
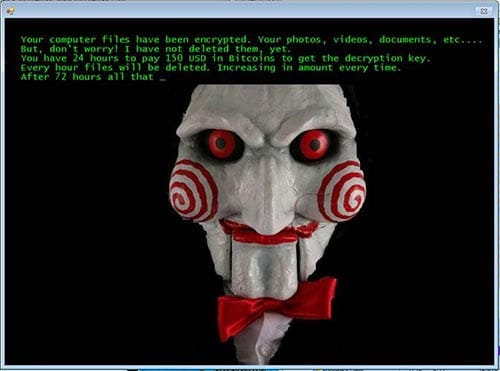
A ransom note left by the Jigsaw ransomware.
When a file is encrypted by ransomware, the file itself is still there and can still be returned to normal. But to do this, it needs to de decrypted using a decryption key, and for most sophisticated ransomware infections, only the crook knows (or is able to provide) that decryption key.
The victim will usually be left instructions on how to pay for a decryption key. Instructions that are either displayed by the ransomware itself or delivered separately by the crooks after the infection.
Sponsored Content. Continued below...
Can I get my files back without a decryption key?
This depends on the ransomware itself. Ransomware has been around for a number of years, and early versions would only use basic encryption techniques to encrypt files that could easily be reversed without a decryption key. However, ransomware has become increasingly sophisticated, and many modern versions can encrypt files using methods that are effectively unbreakable, meaning a decryption key would be necessary.
It ultimately depends on the sophistication and age of the ransomware, and whether security experts have managed to create a decryption method for the particular type of ransomware that infected the victim’s device.
Will paying for a decryption key guarantee a victim gets their files back?
The short answer is no, it doesn’t. A victim, after all, is dealing with criminals. In the past, there have been examples of ransomware that didn’t or couldn’t provide decryption keys after payment, or crooks that provided a decryption key that didn’t work because of design flaws in their malware.
However, it is possible, and in certain cases, likely that someone can get their files back with a decryption key. As ransomware has grown in sophistication, many cyber crooks have seen this type of malware as a long-term money making venture, and as such there is an advantage for the crooks to ensure that paying victims have their files decrypted. After all, if crooks routinely refused to provide the decryption key after payment, soon enough victims would stop paying up for a decryption key they’d know that they probably wouldn’t get.
It is worth noting, however, that most security professionals don’t recommend paying in most circumstances, since doing so fuels the growth of the ransomware industry and provides impetus for the crooks to continue with this illegal endeavour.
Sponsored Content. Continued below...
How do I remove ransomware?
Since ransomware is a type of malware, removal of ransomware is for the most part the same as if you were removing any other type of malware.
For laptops and PCs, this means booting up the device in Safe Mode and running your security software, doing a full system scan and restoring your software to an earlier date using Windows inbuilt Restore Points. The below video goes into more detail.
However removing ransomware doesn’t decrypt your files. While you can remove the infection, you cannot remove the damage caused by the infection this way.
How do I avoid ransomware?
Ransomware is still malware, and it spreads in the same way as most other types of malware, so to avoid it you should follow general security advice.
– Make sure your software, including your operating system, is up-to-date and supported.
– Don’t open suspicious or unexpected email attachments.
– Don’t allow files to download to your computer from the Internet unless you know what they are and that you are on a trusted website.
– Have good, reliable antivirus software installed, whether it is a free version or a full, premium version. Our editor’s choice premium security software is below.

Data back-ups are the best defence against a successful ransomware infection
You should backup your data regularly so if your files are encrypted, you don’t need to consider buying a decryption key from crooks to get your files back since you can retrieve them from your backup solution. Our recommended backup solutions are here.
Ultimately, following good security habits and always ensuring you have a recent backup of your important data are the best defences against any potential ransomware infection.
Further Reading…
10 emails that tried to trick us into installing ransomware on our computer.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
