What is a spear-phishing scam?
We discuss what a spear-phishing scam is, how they work and most importantly how to avoid them.
A spear-phishing scam is essentially a targeted phishing scam used to lure victims into handing over personal information to who they believe is a trusted entity, but is actually a criminal. Spear-phishing scams are commonly target specific organisations.
Since spear-phishing scams are targeted phishing scams, we’ll begin with describing what phishing scams are. A phishing scam is any scam used to trick a victim into handing over sensitive information – for example account usernames and passwords. This is accomplished by tricking the victim into believing they are handing over that information to a trusted entity. It’s called “phishing” because criminals are essentially ‘fishing’ for sensitive information to see who ‘bites’ and falls for the scam.
Commonly, phishing scams are orchestrated over email or social media messaging services (like Facebook Messenger.) The criminal contacts the victim pretending to be a trusted entity, such as their bank, PayPal or Facebook for example. The criminal will trick the victim into handing over sensitive information using a social engineering technique.
Such techniques can involve tricking the victim into clicking a link that leads to a spoof login page that requests a username and password – data that is subsequently sent to the criminal.
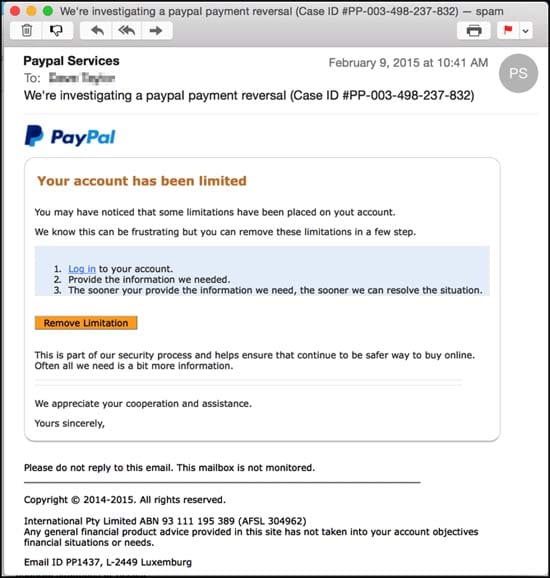
A typical phishing email pretending to be from PayPal
Phishing scams are usually sent to hundreds, thousands or millions of Internet users to see who falls for the scam. This can be achieved, for example, by sending the same phishing scam to a database of many email addresses. As such, phishing scams are generic scams that contain little or no personal information relevant to the victim (for example, the criminal may send a victim an email pretending to be a bank that the victim isn’t even a customer of) and consequently the success rate is typically quite low.
Spear-phishing represents the targeted version of phishing. This means the criminal has obtained information relevant to the victim – such as their whole name, address, workplace, names of co-workers – and they have tailored their scam to include this information to make it more convincing.
Sponsored Content. Continued below...
As such, spear-phishing scams are tailored to target specific victims in order to trick them into handing over sensitive information under the belief that they are communicating with a trusted entity. Well designed spear-phishing scams can have a high success rate and are often used to target employees of corporations and can be used to obtain employee login credentials, sensitive financial information related to a business, employee information or trade secrets.
An example of a spear-phishing scam could be criminal sending an email to specific employees of a business (whose names and emails could have been obtained from the company website) where the criminal poses as the company CEO (again the name could have been obtained from public company records) requesting sensitive company information, such as information on the company’s finances.
Avoiding spear-phishing scams can be tricky if the scam itself it well designed and targeted. The advice for potential victims would be treating any email or electronic communication requesting sensitive information as suspicious, and limit situations where requesting sensitive information in such a manner would be considered acceptable.
Additionally, always be aware what information about a company is publicly available to cyber-criminals and as such do not automatically afford any electronic communication containing such information with any credibility, especially if they contain email attachments or links to webpages requesting sensitive information such as usernames or passwords.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
