The ILOVEYOU worm. The love letter that caused global chaos
Exactly 20 years before the coronavirus pandemic escaped China and caused alarm around the world, another pandemic was spreading from country to country.
Just like COVID-19, there was little immunity to it, since no one had seen anything like it before. Just like COVID-19, it had the potential to cause damage ranging in the billions. And just like COVID-19, it was infecting millions.
Only it wasn’t infecting humans. It was infecting Windows PCs.
In May 2020, the ILOVEYOU computer malware – also referred to as THE LOVE BUG worm – celebrates its 20th birthday. Widely regarded as one of the most virulent cases of malware ever, it was one of the first examples of a computer worm managing to infect millions of computers from all around the world. It was also the first example of malware using a simple social engineering trick to such devastating success.
In fact, so popular and widespread was the ILOVEYOU malware, the same month it was released into the wild, it made its way to the front cover of TIME Magazine.
The ILOVEYOU malware was created in the Philippines by a computer sciences student called Onel de Guzman. It was released on an unwary and unsuspecting public during the first week of May 2000. Windows XP wouldn’t exist for another year, and the most recent consumer Windows operating system was Windows 98, (though its predecessor, Windows 95 was still extremely popular.) Most consumers were still connected to the Internet via the whiny whir of dial-up Internet. During those comparatively archaic times, Internet surfers had a username and password given to them by their Internet Service Provider which they needed to enter before their computer dialled up.

ILOVEYOU was designed to steal those passwords (Guzman struggled to afford Internet access.) Not only that, it would wreak havoc on a user’s computer by overwriting certain types of files, such as Office documents, JPG images and important Windows files, rendering a computer unbootable.
Like many types of malware today, ILOVEYOU arrived in the form of a dangerous email attachment that – if opened – would install malware on the computer. In today’s digital world, opening unexpected email attachments is (or at least should be) ingrained on the majority of people as a big NO-NO. But in the year 2000, malware-laden email attachments were still very much a novelty.
Sponsored Content. Continued below...
But perhaps the ILOVEYOU malware owed its then unprecedented success to its social engineering. That’s the non-technical component of a scam. In this case, how does a scammer lure so many email recipients into opening a dangerous attachment and thus compromising their own security? It was so incredibly simple. A love letter. Regardless of marital status or level of interest, a love letter sent straight to your email is a difficult thing to just ignore. It would pique the curiosity of just about anybody.
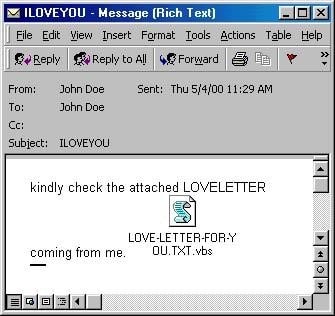
In most cases, the email contained an attachment called LOVE-LETTER-FOR-YOU.TXT.vbs. Notice the two file type extensions, txt and vbs. The txt extension is fake, and used to trick recipients into thinking the attachment was a harmless text file that would probably open in Notepad. That illusion was heightened by email clients including Microsoft Outlook that would hide the real extension of the attachment (vbs – Visual Basic Scripting) as was standard at the time for file types that Windows recognises. That meant recipients only saw the .txt extension.
And when the recipient opened the attachment, the malware installed itself. Upon installation, not only did it play havoc with files stored on the computer, it created a duplicate of itself and sent itself to any email addresses stored on a user’s Outlook address book. This resulted in the victim sending out an identical “love letter” attachment to their email contacts, and thus it spread from one user to another. This self-replicating ability meant that the ILOVEYOU malware could be best described as a computer worm.
Sponsored Content. Continued below...
ILOVEYOU found itself in the wild on May 4th 2000. Within 24 hours, it had spread from the Philippines to Singapore, then to Europe and then to the United States. It is estimated to have infected over 40 million machines, and caused the shutdown of email networks in countless businesses, reportedly affecting the Houses of Parliament and even The Pentagon.
The cost in terms of actual damages varies, but even conservative estimates place it in the region of hundreds of millions of dollars. By May 6th 2020, it was considered by many experts to be the most disruptive examples of malware to date.
Going through the code of ILOVEYOU, investigators soon tracked down the author of the malware, Onel de Guzman in Manila, Philippines. De Guzman, a computer sciences student, had just had his thesis rejected by his AMA Computer College peers. The thesis, incidentally, proposed the distribution of a password-stealing computer worm designed to provide free Internet access to those that struggled to afford the cost to go online. The AMA Computer College dismissed his thesis as “illegal”.
A week after ILOVEYOU spread, de Guzman admitted that the malware was “possibly” his creation, but had been leaked online accidentally. One could speculate that this was likely the advice of his lawyer, who would have known that Filipino law would require intent in order to prosecute under [then] legislation surrounding destruction of property. If the malware was leaked accidentally, there was no intent.
De Guzman was later released, and not a single person was ever prosecuted for the ILOVEYOU malware, or the destruction is caused around the world.

Fast forward 20 years, and the information security world is vastly different. But de Guzman has hardly been forgotten. In 2020, investigative reporter Geoff White tracked de Guzman down to a shopping mall in Manila. Guzman subsequently confessed that he had released the malware in order to steal passwords to let him access the Internet. He told White that he regretted the damage his malware had caused.
The ILOVEYOU malware campaign is a significant entry into the ever changing journal of information security. While the 20-year old malware has now been surpassed in terms of devastation and infection numbers, it still represents an important moment that would forever alter the course of the digital security landscape. It was perhaps the first prolific example highlighting how social engineering is possibly the most vital crux of any malware campaign, and the perfect demonstration revealing the extent, even 20 years ago, of how much we rely on the infinite maze of cables and drives, and the consequences that occur when those cables and drives all go wrong.
Continued below...
Thanks for reading, we hope this article helped, but before you leave us for greener pastures, please help us out.
We're hoping to be totally ad-free by 2025 - after all, no one likes online adverts, and all they do is get in the way and slow everything down. But of course we still have fees and costs to pay, so please, please consider becoming a Facebook supporter! It costs only 0.99p (~$1.30) a month (you can stop at any time) and ensures we can still keep posting Cybersecurity themed content to help keep our communities safe and scam-free. You can subscribe here
Remember, we're active on social media - so follow us on Facebook, Bluesky, Instagram and X
